Introduction
Every year, software teams release thousands of new applications into the world. Businesses rely on these apps to power e-commerce, manage supply chains, support customers, and protect sensitive data. But as applications become more complex, so do the threats they face.
In 2025, the stakes are higher than ever. Regulatory changes are reshaping compliance requirements. Attackers are using AI-driven exploits to find weaknesses faster. And organizations are under pressure to integrate security into every layer of their custom software and IT services.
In this guide, we’ll explore application security best practices that matter today, highlight emerging trends, and explain how to align with cybersecurity regulation changes in 2025. Whether you are a CTO, developer, or IT manager, this article will give you the roadmap to strengthen your security posture while keeping development agile and customer-focused.
Why Application Security Matters More Than Ever

- Escalating cybercrime costs: According to Cybersecurity Ventures, global cybercrime damage is expected to hit $10.5 trillion annually by 2025. Applications are prime targets.
- Shift-left development: Modern teams are adopting DevSecOps to embed security early in the software lifecycle.
- Global regulations tightening: Privacy and security laws in the U.S., EU, and Asia require stricter compliance and reporting.
- Trust as a business driver: Customers won’t use software they don’t trust. Security is now a selling point, not just a risk management checkbox.
Core Application Security Best Practices
These best practices form the foundation of secure software development in 2025.
1. Secure by Design
Building security into your app from the first line of code is non-negotiable. Follow frameworks like Secure by Design Principles, which emphasize:
- Minimal attack surface
- Least privilege for every component
- Strong defaults instead of optional security
Pro tip: Conduct threat modeling workshops during the planning stage. Anticipate risks before they appear.
2. Regular Security Testing
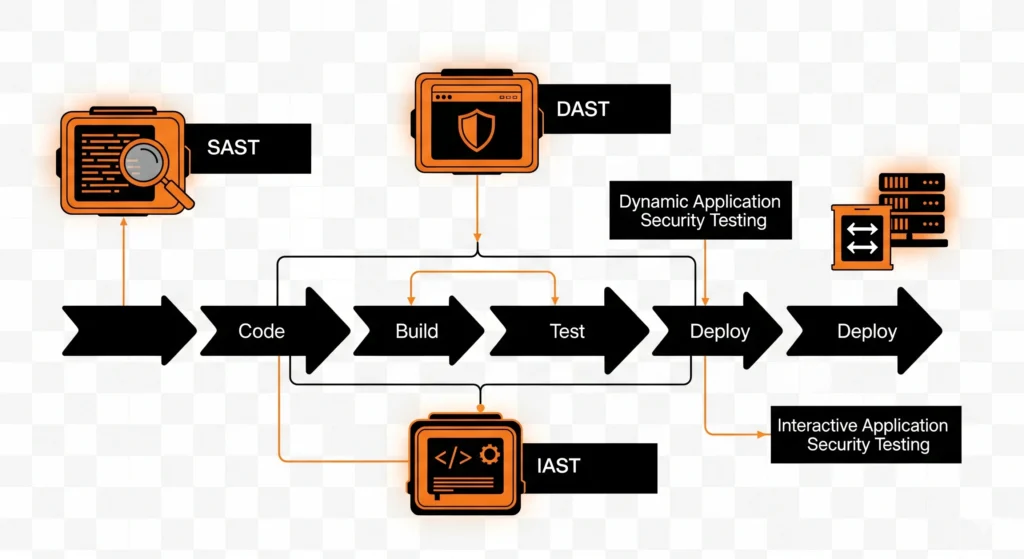
Static and dynamic testing are still essential, but now interactive application security testing (IAST) is gaining traction because it integrates directly into CI/CD pipelines.
- SAST (Static Application Security Testing) – scans source code for vulnerabilities.
- DAST (Dynamic Application Security Testing) – checks running applications for runtime flaws.
- IAST – combines both during runtime, giving developers actionable insights immediately.
3. Protect APIs as First-Class Citizens
In 2025, APIs are often the biggest attack vector.
- Enforce strong authentication (OAuth 2.0, OpenID Connect).
- Validate input/output rigorously.
- Use rate limiting and throttling to mitigate abuse.
- Apply API gateways and Zero Trust network models.
4. Patch and Update Continuously
The Log4j crisis taught us a painful lesson: outdated dependencies are ticking time bombs.
- Automate dependency scanning with tools like Dependabot or Snyk.
- Maintain a software bill of materials (SBOM) for compliance.
- Apply security patches within hours, not weeks.
5. Enforce Strong Identity and Access Management
With the rise of remote and hybrid work, IAM is critical:
- Multi-factor authentication everywhere.
- Role-based access controls.
- Just-in-time access for privileged accounts.
Pro tip: Consider passwordless authentication (FIDO2, biometrics) for user-facing apps.
6. Encrypt Data in Transit and at Rest
Encryption is table stakes, but misconfiguration is common.
- Use TLS 1.3 for all communications.
- Enforce full-disk encryption on servers.
- Manage encryption keys centrally and rotate regularly.
7. Secure the Software Supply Chain
Attackers don’t just target your code — they target your third-party libraries, vendors, and build systems.
- Adopt Zero Trust for supply chain access.
- Digitally sign all builds and artifacts.
- Vet vendors against compliance and security certifications.
Application Security Trends to Watch in 2025
Beyond the fundamentals, organizations need to anticipate the future. These application security trends are shaping strategies in 2025.
Trend 1: AI-Driven Security
AI is a double-edged sword:
- Defensive use: AI can detect anomalies, predict threats, and triage incidents faster than humans.
- Offensive use: Hackers are leveraging AI to craft polymorphic malware and automated exploits.
Invest in AI-powered security tools but never fully outsource decision-making to machines.
Trend 2: Zero Trust as Standard
What started as a buzzword is now mainstream. By 2025, Zero Trust Architecture (ZTA) is widely adopted, not just for networks but for applications:
- Every API call, microservice, and user request is authenticated and authorized.
- No implicit trust within internal networks.
Trend 3: Regulatory Pressure
More on this below — but in short, expect mandatory disclosure laws, stricter fines, and expanded liability for insecure apps.
Trend 4: Secure Cloud-Native Development
With most new apps deployed in Kubernetes and serverless environments:
- Security needs to be container-aware.
- Policies must follow workloads across multi-cloud setups.
- Misconfigurations remain the #1 cloud vulnerability.
Trend 5: Developer-Centric Security Tools
Legacy tools frustrated developers. The new wave of security tools are:
- Embedded in IDEs (real-time feedback).
- Automated in CI/CD pipelines.
- Developer-friendly, reducing friction between security and speed.
Cybersecurity Regulation Changes in 2025
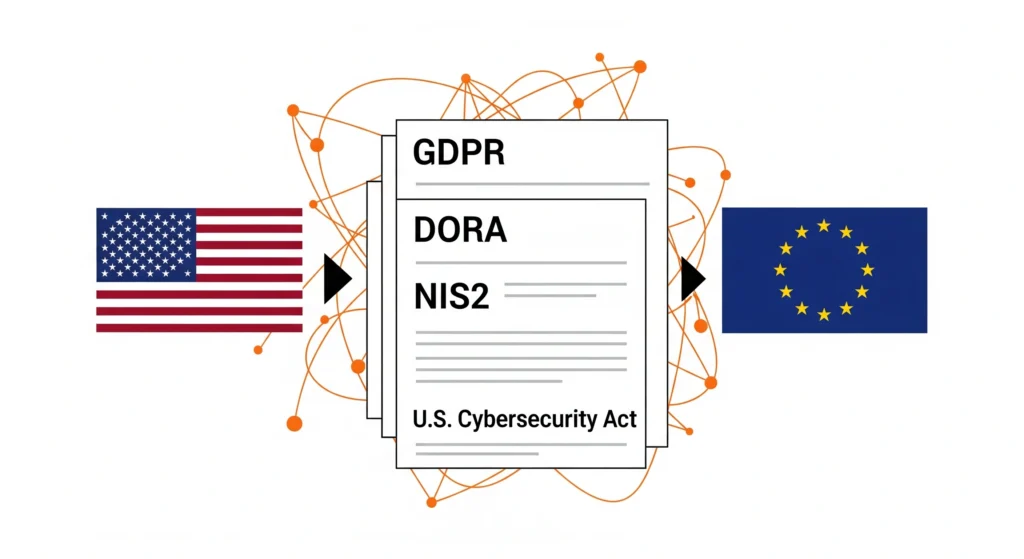
Application security doesn’t exist in a vacuum — regulations are changing the way software is built and delivered. Here’s what to expect in 2025:
-
United States:
- The White House’s National Cybersecurity Strategy is introducing stricter liability for software vendors who ship insecure code.
- State-level privacy laws (California CPRA, Virginia CDPA) continue to expand requirements around user data.
-
European Union:
- NIS2 Directive and Digital Operational Resilience Act (DORA) enforce mandatory security controls and reporting.
- Heavy penalties for non-compliance.
-
Global:
- Countries like India, Brazil, and Singapore are enacting data protection and breach notification rules.
- ISO/IEC 27001 updates require stronger supply chain controls.
Align your custom software IT services with these evolving frameworks. Compliance is no longer optional — it’s a competitive differentiator.
Application Security for Custom Software and IT Services
When building custom applications for clients, IT service providers have a dual responsibility:
- Protect the client’s sensitive data.
- Future-proof the solution against compliance and threat evolution.
Key Strategies for IT Services Providers:
- Perform secure code reviews as part of deliverables.
- Offer managed detection and response (MDR) for ongoing protection.
- Provide compliance mapping to help clients meet regulations.
- Educate clients on secure usage — security doesn’t stop after deployment.
Frequently Asked Questions
Q: What is the most important application security best practice?
Ans: Secure design from the start. Retrofitting security later is more expensive and less effective.
Q: How do cybersecurity regulation changes in 2025 affect small businesses?
Ans: Even small businesses must comply with disclosure and data protection laws. Many regulations now apply regardless of company size if sensitive data is processed.
Q: What trends are shaping application security?
Ans: AI-driven attacks, Zero Trust adoption, supply chain security, and regulatory compliance are leading the way.
Practical Checklist for 2025
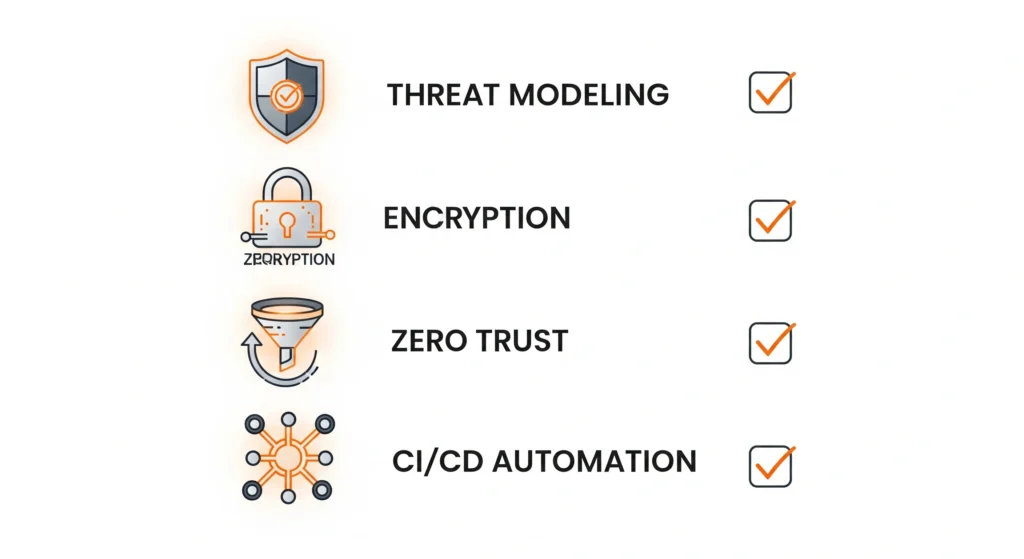
- Conduct regular threat modeling
- Automate security testing in CI/CD
- Harden APIs and enforce Zero Trust
- Patch dependencies rapidly
- Encrypt data everywhere
- Monitor compliance with NIS2, DORA, and U.S. frameworks
- Train developers continuously
Conclusion
In 2025, application security is not a one-time checklist but an ongoing strategy. As regulations evolve and attackers grow more sophisticated, organizations must embrace security as part of their culture.
By following application security best practices, staying ahead of trends, and adapting to cybersecurity regulation changes in 2025, you can ensure your applications remain resilient and trusted.
Custom software and IT services providers have an even greater opportunity: to become trusted partners who deliver not only functionality but also peace of mind.
Secure your applications with confidence — Partner with VirtueNetz today.
 ?>
?>
 ?>
?>
 ?>
?>
 ?>
?>
 ?>
?>